Introduction
Admin’s Guide To Azure Best Practices
Chapter 1
Azure best practices help organizations optimize Azure resources to build and manage secure, reliable, scalable, and cost-effective solutions in the Microsoft Azure cloud. With Azure acting as the backbone of many modern enterprises, getting Azure best practices right can make or break a business.
In this intro to our Azure Best Practices Guide, we’ll review the fundamental best practices every Azure administrator needs to know. Then, in the chapters to follow, we’ll explore specific domains in more depth.
The table below is an overview of the Azure best practices we’ll cover here.
Fundamental Azure Best Practices
| Area | Best practice | Rationale |
|---|---|---|
| Security | Enable Azure AD Conditional Access, enforce MFA | Secure access to Azure resources and Microsoft 365 applications. |
| Disable RDP/SSH from the Internet, use JIT and Azure Bastion | Grant remote access to Windows and Linux VMs in Azure from anywhere without compromising security. | |
| Governance | Secure privileged access with Azure AD PIM | Govern privileged access to mitigate the risk of excessive, unnecessary, or misused access to important resources in your organization. |
| Management | Use Resource Groups; Tag all resources | Group related resources into containers for ease of management, security, and cost tracking. Tag resources for communication and discovery. |
| Operations | Enable Azure AD Self-Service Password Reset; Unlock users, reduce support calls. | Reduce the number of support calls, save money, and boost productivity by empowering users to change/reset their passwords securely and quickly. |
| Use Azure Advisor to benchmark and optimize your deployments as per Microsoft best practices | Link recommendations with remediation steps to optimize and improve business continuity. | |
| Uptime and Performance | Scale-out and scale-in with automatic horizontal scaling. | Get Azure to manage your applications’ availability, redundancy, and performance. |
| Cost Optimization | Use reserved instancesLeverage Azure AdvisorRemove unneeded resourcesUse Standard SSD or Standard HDD Auto-stop/start non-critical VMs | Pay for what you use, use what you pay for |
Fundamental Azure Security Best Practices
Enable Azure AD Conditional Access and enforce MFA
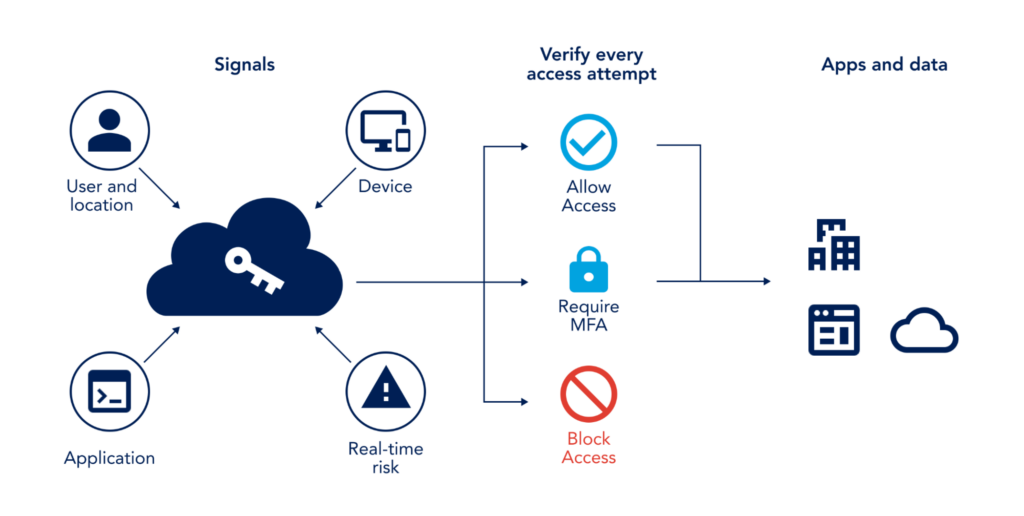
Restricting access to Azure resources and Microsoft 365 applications is a critical component of security posture in Azure. Administrators must strike the right balance between security and usability to mitigate risk without stifling productivity.
Azure AD Conditional Access helps admins empower users to be productive wherever and whenever, and at the same time, protect the organization’s assets. Conditional Access helps automate access control based on security, business, and compliance conditions. Azure AD Multi-Factor Authentication adds an essential security layer to safeguard Access to data and applications. Visit these Azure documentation pages to plan an Azure Active Directory conditional access deployment, and review deployment considerations for Azure AD Multi-Factor Authentication (MFA).
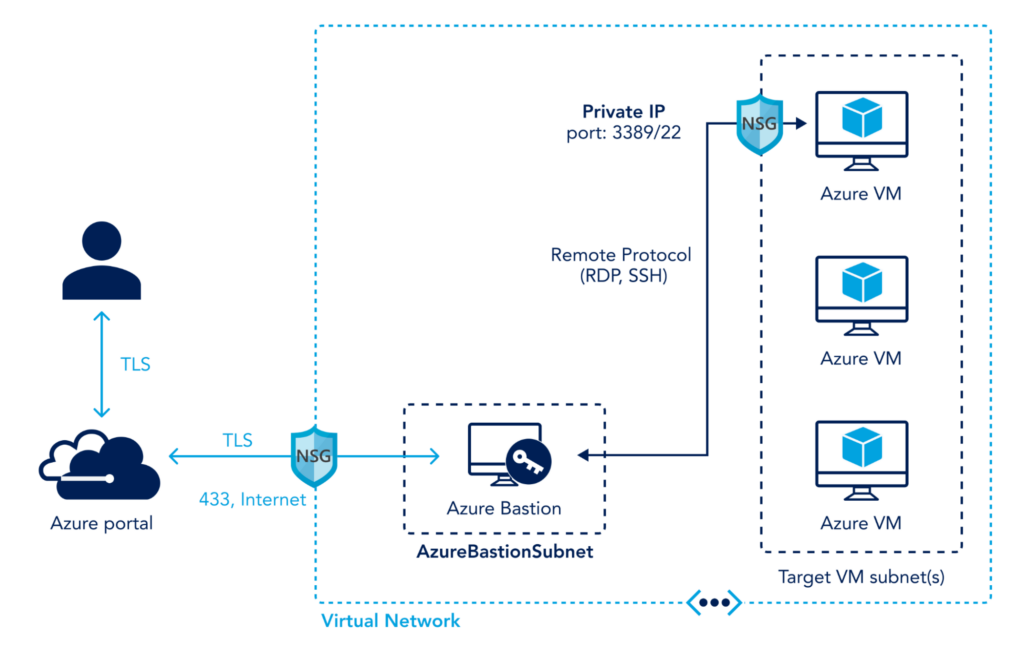
Disable RDP/SSH from the Internet- Use JIT and Azure Bastion
To grant remote access to Windows and Linux VMs in Azure from anywhere in the world without compromising security, do not expose RDP and SSH access over the Internet. Instead, use one of these methods to enable secure remote access to Azure virtual machines:
- Enable Just-In-Time (JIT) VM access over site-to-site VPN or ExpressRoute connections. JIT provides time-bound VM access via RDP and SSH, which helps reduce brute force attacks exposure. Essentially, Network Security Groups (NSGs) lockdown RDP and SSH ports and only open them for a set period (e.g., 3 hours) to authorized users. JIT VM access uses Azure AD and Role-Based Access Control (RBAC) permissions for users to request access.
- Configure Azure Bastion inside your virtual network. Azure Bastion provides secure and seamless RDP/SSH connectivity to your VMs directly from the Azure portal over TLS. Azure Bastion service is a PaaS service that eliminates the need for VMs to have public IP addresses, agents, or special client software.
Fundamental Azure Governance Best Practices
Secure privileged access with Azure AD PIM
Manage, control, and monitor access to critical resources in Azure, Microsoft 365, and Intune with Azure AD Privileged Identity Management (PIM). Through PIM, admins must activate or elevate their privilege to use it for a limited time. PIM policies apply on Azure AD roles (e.g., Global, Billing, Exchange Administrator roles) and Azure resource roles (e.g., subscription owner, VM contributor). Visit this Microsoft documentation page to plan a Privileged Identity Management (PIM) deployment.
Fundamental Azure Management Best Practices
Use Resource Groups; Tag all resources
Plan, design, and implement a resource group strategy that fits your business needs. As a logical collection of Azure resources, resource groups are used to group related resources into containers for ease of management, security, and tracking costs associated with your workloads.
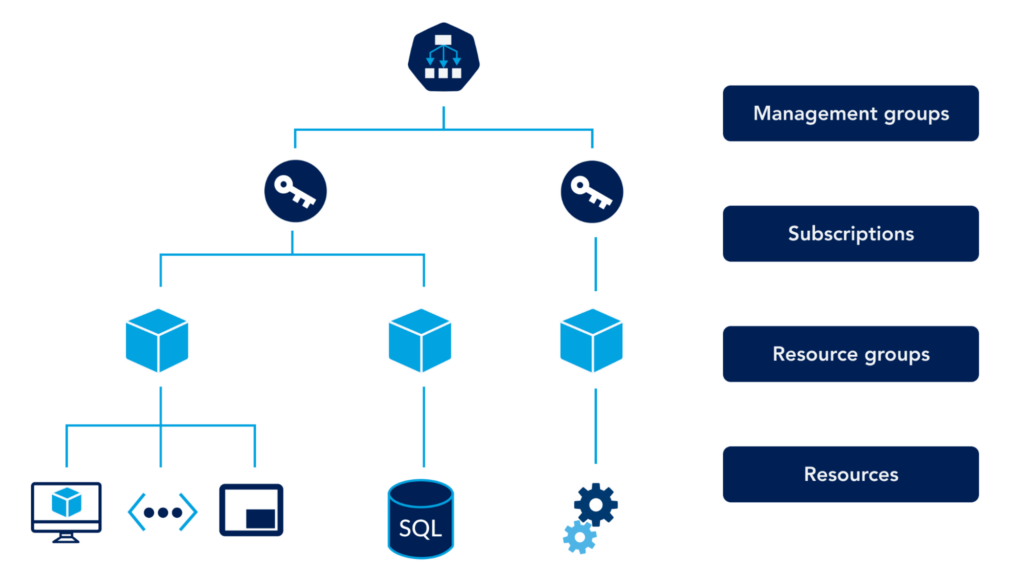
A best practice resource group strategy should include the following:
- Group resources by
- Environment: e.g., production, development
- Application: e.g., payroll, billing
- Business Unit: e.g., IT, HR
- Follow a well-defined naming standard
Include resource type, application or business unit, environment, Azure region, and consecutive entity number. For example, VM-app1-prod-Apac-01 denotes the first production VM for the application app1 deployed in the APAC region. - Leverage Resource tagging
Tag all resources inside resource groups to communicate valuable information to your teams, discover resources, and manage costs.
Fundamental Azure Operations Best Practices
Enable Azure AD Self-Service Password Reset- Unlock users and reduce support calls
When you give users the ability to change or reset their passwords without any assistance from the helpdesk, you reduce IT’s support burden and boost productivity. Azure AD self-service password reset (SSPR) supports granular enablement and configuration, including the number of authentication methods and methods required for a password reset. SSPR also supports customization and email notifications.
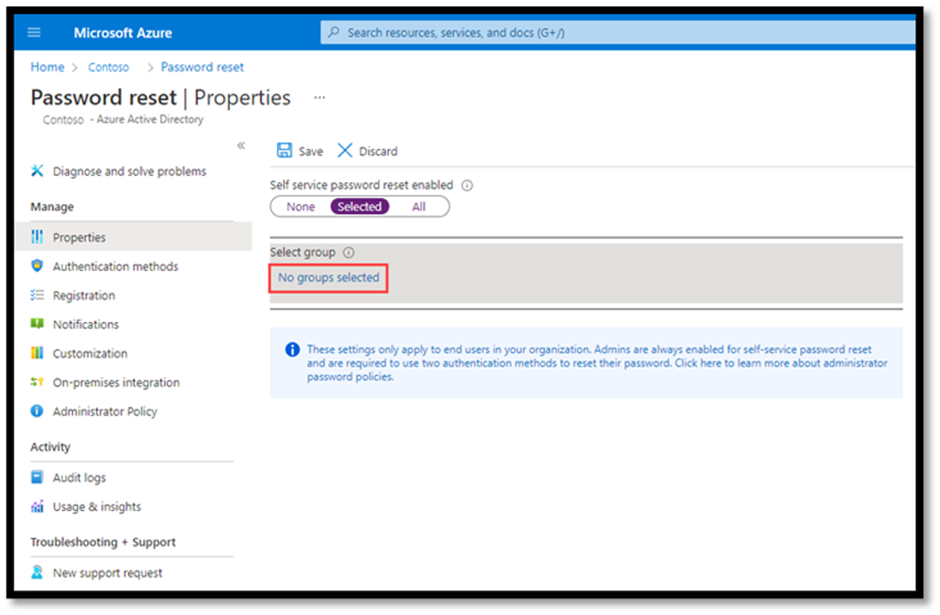
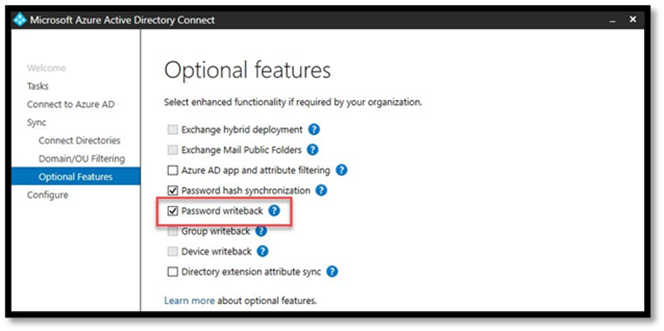
In Azure AD hybrid environments, password resets can be synchronized to on-premises AD. To enable this functionality, select the “Password writeback” optional feature in Azure AD Connect (AADC), and enable “On-premises integration” in SSPR.
Use Azure Advisor, your personalized cloud consultant
Azure Advisor provides personalized, actionable cost, security, reliability, operational excellence, and performance recommendations. Azure Advisor helps organizations optimize their deployments as per Microsoft best practices. These recommendations are gathered from resource configuration analysis and usage telemetry in your Azure tenant and are based on Microsoft best practices that work for most organizations.
To help implement the recommended best practices, Azure advisor links the recommendations with remediation steps. Admins can follow the provided step-by-step implementation guides to implement the suggested solutions. Admins can also postpone remediations or remove them if not applicable to their environment.
Fundamental Azure Uptime & Performance Best Practices
Use autoscaling and let Azure manage your applications’ availability, redundancy, and performance.
The dynamic allocation of resources to match performance requirements is called autoscaling. Autoscaling helps with the availability, redundancy, and performance of business applications in Azure. It also removes idle resources when they are no longer needed, ultimately saving costs.
Azure virtual machine scale sets and Azure app services are two examples of autoscaling.
- Virtual machine scale sets allow admins to create and manage a group of load-balanced VMs based on demand. The demand can be defined based on user-defined performance criteria (e.g., percentage CPU, network in, disk read operations/sec) or set schedules. VMs can increase or decrease in response to the expressed demand. In addition to redundancy and improved performance, virtual machine scale sets provide central management, configuration, and updates to a large number of VMs, big data, and containers.
- Azure app services support scale-up, scale-out, and autoscaling. Admins can get more resources and extra features for their web apps in a scale-up workflow. In scale-out, the number of VMs running the apps can increase to a maximum of 30 instances. Autoscaling leverages the platform’s logic to automatically scale App services, providing hassle-free application management, scalability, and performance.
App services autoscaling is only supported in standard, premium, and isolated pricing tiers. Admins must configure autoscaling to scale up or down based on defined rules or set schedules. Like virtual machine scale sets, app services autoscaling works on user-defined performance criteria (e.g., percentage CPU, network in, disk read operations/sec) or set schedules (e.g., scale up to x number of instances on Fridays and Saturdays).
Fundamental Azure Cost Optimization Best Practices
Pay for what you use, use what you pay for
Paying for what you use in Azure is both art and science. The art is in selecting the right resources from the beginning, and the science is in stopping and starting these services at the right time.
These five best practices are great starting points for cost optimization in Azure:
- Use reserved instances. Reserved instances make sense in specific scenarios; for example, if you permanently use a particular VM size on several VMs. A good example is domain controllers running in Azure. Three-year reserved instances can save up to 72% on these VMs
- Consult Azure Advisor. Cost optimization recommendations in Azure Advisor are based on Microsoft best practices. The data is gathered from your tenant’s usage analysis and benchmarked against Microsoft global Azure deployments. Azure Advisor provides proper guidance on cost optimization in Azure.
- Delete unneeded resources. Often, orphan resources are overlooked and left in a tenant after VMs are removed. These resources incur costs! Network cards and OS disks are common examples of these Azure orphan resources. Fortunately, the Azure Portal helps remind administrators at provisioning and deletion time to remove unneeded resources.
Tick the box “Delete NIC when VM is deleted” to remove associated NICs. If this VM has a public IP address, tick the “Delete public IP and NIC when VM is deleted”. These options appear in the networking section of VM provisioning pages.
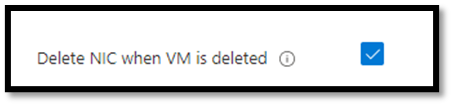
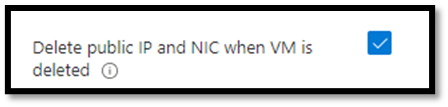
Deleting unassociated NICs in Azure.
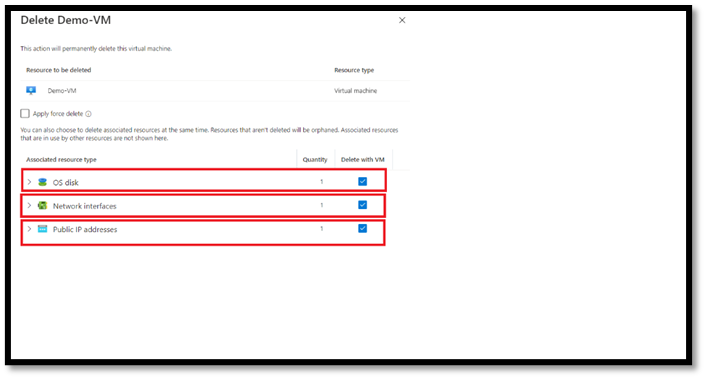
To remove the associated OS disk, make sure OS disk is selected as one of the “associated resource types” to be deleted when VM is deleted. These options appear when you delete a VM.
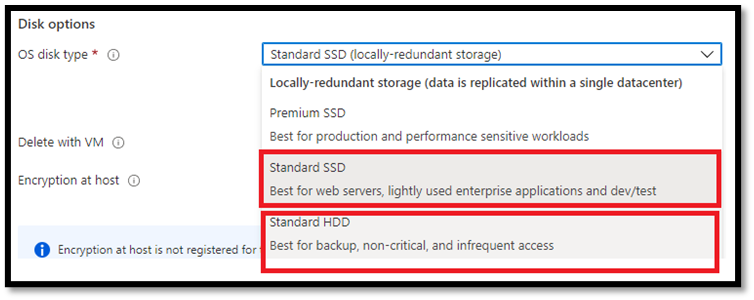
- Use Standard SSD or Standard HDD when appropriate. In development and test environments, you can save up to 70% on OS storage cost if you select anything but Premium SSD as your OS disk type. The supported OS disk size for Windows is 127 GiB. These disks cost $19.71 for Premium SSD, $9.60 for Standard SSD, and $5.89 for Standard HDD. These charges accrue monthly regardless of VM state. In other words, OS disks on started and stopped VMs cost the same.
- Auto-stop/start non-critical VMs. Stopping (deallocating) VMs in Azure stops the charges. Non-critical VMs can be stopped (deallocated) when not in use. Let’s use A Standard A4 v2 VM as an example. Currently, it costs $137.52/month. If it isn’t running critical workloads and can be shut down after hours and on the weekend, the monthly charges decrease to $50.42. That is almost 65% saving. To reduce VM costs, use Azure automation runbooks to auto-stop and start VMs based on business rules (e.g., schedule, order, performance metrics).You can learn more about automatically starting and stopping VMs in the official Microsoft documentation.
Want to Learn More Azure Best Practices?
We’ve only scratched the surface of Azure best practices here. To help you dive deeper into the technical side of Azure and get the most out of the platform, we’ve created a detailed Azure Best Practices Guide. Each chapter in the guide covers an important aspect of Azure and provides you with details on proven best practices.
Chapter 1:
Azure security best practices
Chapter 2:
Azure SQL vs SQL server
Chapter 3:
Azure lab services
Chapter 4:
Azure resource group best practices
Chapter 5:
Azure migration services
Chapter 6:
Azure firewall vs. NSG
You like our article?
Follow our monthly hybrid cloud digest on LinkedIn to receive more free educational content like this.